Application Penetration Test
Application Penetration Test
The package is designed to perform the thorough Penetration Test to satisfy regulatory, tender or compliance requirements. It is suitable to applications with multiple user roles and applications that are API based.
The test is performed by senior certified penetration testers (based in Australia). The methodology is based on OWASP and NIST standards. Penetration testing report will help to meet regulatory obligations, tender requirements, customer’s security policies and PCI DSS / ISO27001 requirements.
Web Application Penetration Testing Methodology
Lean Security performs a comprehensive web application penetration test to reduce the risk of the compromise and improve compliance. The methodology is aligned with the best practices from NIST and OWASP. The penetration test is performed by the senior security consultants with CISSP, CISA, CISM, GCIH, GPEN, GWAPT, GXPN certifications.
Main features and benefits:
Comprehensive web application penetration tests help determine the well-known and “Zero day” security issues on the target web site
Thorough risk assessment helps prioritise the remediation actions
Compliance assessment and customised report templates
Penetration testing report can be used during the external compliance and certification processes, such as ISO27001, PCI DSS, SOC 2 certifications etc.
The testing is executed based on the following methodology:
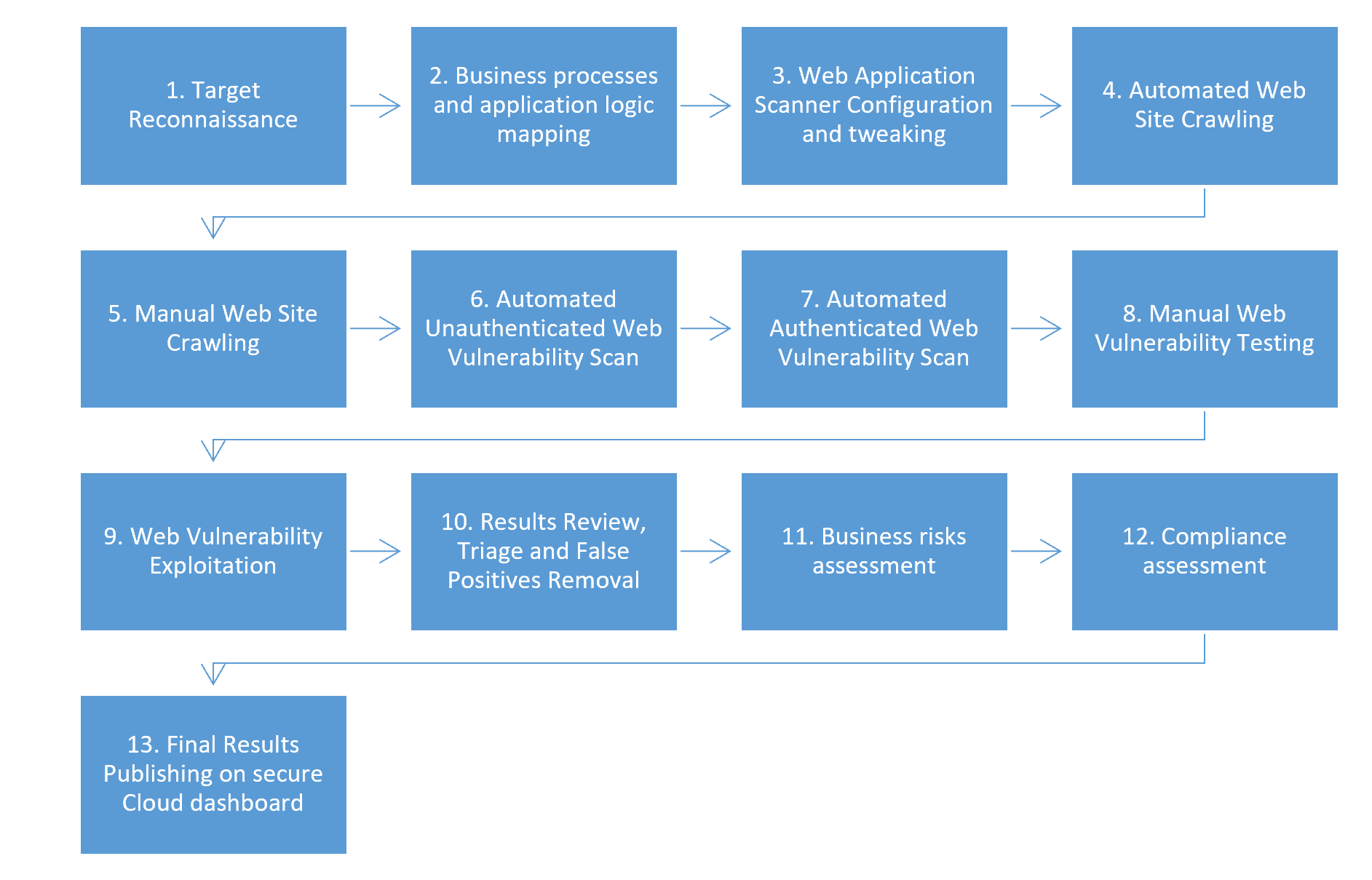
Step 1. Target reconnaissance.
The Lean Security engineer will receive the information about the target you would like to assess. The information includes the web application URL, business criticalities etc. The engineer will then manually connect to the target to confirm that the web site can be reached and scanned. The engineer will also do a sample check of the pages and subfolder to make sure the target web site operates correctly. During this step, the engineer will also determine the backend technology used for the web application (Wordpress CMS, Drupal, Joomla, commercial CMS etc).
Step 2. Business processes and application logic mapping
The security engineer will manually explore the application and map the business functions it executes and the processes it supports. Depending on the type of the web application (Software-as-a-Service portal, online banking portal, e-Commerce shop etc.) the tester will determine the access control matrix and identify the user privileges levels, permitted actions and the desired outcome.
Step 3. Web Application Scanner Configuration and Tweaking
Lean Security uses multiple web application security scanners to assess the security of the web application. The list of scanners includes both commercial and freeware security tools used by both security professionals and hackers. This step is essential to make sure the scanner covers the whole application and that every page is assessed for security issues. The engineer will also tweak the scanner depending on the website technology and framework (ASP.NET, PHP, AJAX etc). The web scanner configuration is a labour intensive process and our engineers have used their extensive experience and knowledge of the web application issues to optimise the scan performance.
Step 4. Automated Website Crawling
The Lean Security engineer will then instruct the web application scanner to crawl the website and determine which pages are available to an unauthenticated user. The web app scanner will then visit every page of the website and determine the site tree.
Step 5. Manual Website Crawling
The security engineer will review the site tree that was built during the automated web site crawling and then manually verify it. The engineer will also manually crawl the website and determine the areas which were not checkedby the automated scanner. If a target application contains authentication forms or restricted areas, the engineer will manually log in and make sure the restricted areas are crawled and added to the site tree as well.
Step 6. Automated unauthenticated web vulnerability scan.
The engineer will then start the automated security scan in order to determine the security issues on the identified pages. The scanner will test all the web page inputs for the common web application vulnerabilities, such as SQL injection, Cross Site Scripting (XSS), Cross Frame Scripting, Local File inclusions (LFI), Remote File inclusions (RFI), default directories and many other website security issues. The scan will be executed in a controlled and only introduce minimal performance impact on your web application.
Step 7. Automated authenticated web vulnerability scan.
The Lean Security tester then will perform the automated security test on the parts of the target web application that requires logging in. The examples include membership areas, online booking areas, data collection forms, promotion web sites etc. The scan is controlled to ensure that minimum impact is done on the production system or the server infrastructure.
Step 8. Manual web vulnerability testing.
This step includes the actions and tests to identify the vulnerabilities not picked up by the automated security scanner. The engineer will use the custom written tools and manual testing to fuzz the application and determine the loopholes in the application's logic. The tests will take into consideration the application's functions and business processes. The common issues identified during this step are the password management issues, the account lifecycle management issues, the access control issues, application restrictions bypass etc.
Step 9. Web vulnerability exploitation
The security tester will then try to exploit the identified security issues to determine the business risk of the finding. The Lean Security consultants use open source, commercial and custom written exploits to extract the data from an application. For example, using the SQL injection, it might be possible to dump all the information from the backend SQL database or even take control over an entire web server. If the tester finds the unprotected file's upload functionality, it might be possible to upload the web shell to execute the system commands. The exploitation is done manually in a controlled environment to ensure the security of the extracted data. The tester will also ask for an explicit permission before exploiting the vulnerability.
Step 10. Results Review, Triage and False Positives Removal
The automated web site vulnerability scanners often produce a lot of false positives. The Lean Security engineer will manually inspect and validate the security issues to remove those false positives. The Lean Security engineer will also perform a triage of the security findings to determine the likelihood, impact and security risk of the identified security issue. This step also helps us tweak the system to minimise the occurrence of false positives in future scans.
Step 11. Business risks assessment.
Based on the results of the automated security scan and manual penetration tests, the security consultant will determine the business risks of the vulnerabilities. Several factors are taken into consideration: The type of data the tester could get access to, the easiness of exploitation and the likelihood of somebody finding the issue. Lean Security uses the comprehensive risks assessment methodology based on the industry's best practices to determine the business risk.
Step 12. Compliance assessment
The findings are mapped to OWASP, PCI DSS or ISO27001 requirements. The reports can be also customised to meet any specific customer or tender requirements.
Step 13. Publishing the results.
When the web application penetration test is completed, the results are published on Lean Security customers’ secure Cloud based dashboard. The customers can log in online and review the results of their security assessment. The dashboard allows the customers to export the results to CSV, PDF or HTML format for offline distribution.