In today’s world, each and every enterprise is choosing to adapt the latest technology and use highly technical devices that are incorporated with the Internet. As it speeds up the operations within a company, it also makes security very crucial.
Potential Threats to Web Applications
One might wonder as to what potential threats are their web applications servers vulnerable to. Well, if we talk about threats, they are too many! Each and every device that is connected to the internet receives a unique IP address. This IP address comprises of two components, namely a host component and a network component.
Controlling Security Risks in Cloud
The world is observing a definite trend Shift as businesses have started moving over to cloud with their data as well as their services. The cloud-computing sector is observing an explosive growth as numerous cloud computing service providers are springing up. As it happened with most technologies in the past, opinions got divided on merit. While most of the analysts deem cloud computing a revolutionary change, a few of them are worried about the control of security risks in cloud.
Why Online Businesses Should Go For Managed and Secure Cloud Hosting Services?
Considered to be the hottest debate today in the information technology community, cloud computing is subjected to some criticism as well as a lot of fame. Those in support of the technology, suggest that the scalability, flexibility, and economics of the cloud; make cloud based website management, a practical and logical choice, while its opponents point out the concerns related to privacy and security, which are reasons strong enough, to not move businesses to the cloud.
The Evolution of E-Commerce amidst Rising Security Concerns
The many competitive advantages of ecommerce cannot be taken lightly. Offering online business and consumers alike a far improved productivity, significant reduction in costs, access and entry into a global business market, ability to provide a much improved customer service and streamlining business processes; are all reasons for brick and mortar businesses to open up their virtual shop.
Protecting Your Network Perimeter: Life on the Edge
Your perimeter security is the first and foremost layer of defense in your network, which is why it’s of the utmost importance to step back and review its design very carefully. The obvious step that you will need to take when it comes to ensuring a sound architecture, is determining what needs to be protected and then designing your network perimeter security in such a way that it can easily adapt according to your needs as they grow or change.
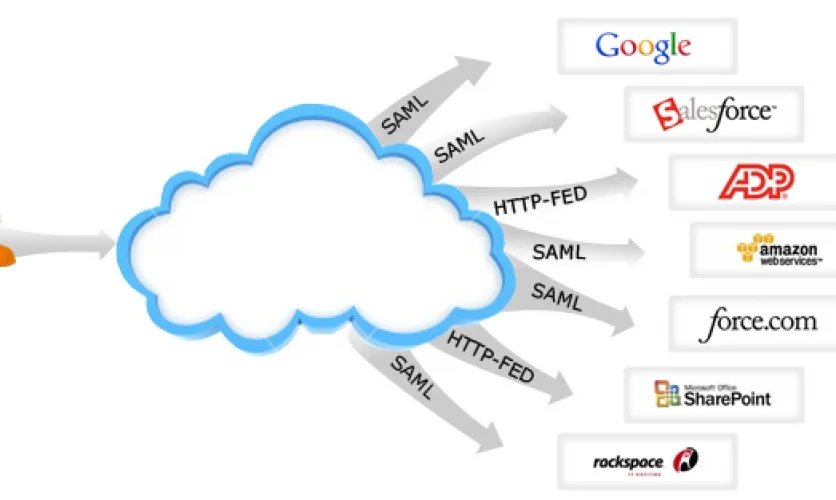
How to Protect and Secure Your Important Data Using SaaS Applications
The size of your company doesn’t matter when it comes to protecting your business’s website network. Hackers will be still attracted to your company’s vital data and information whether it’s a big company, small or just starting out in the field. This is the reason why, having a rock solid security defense of the network is of the utmost importance.
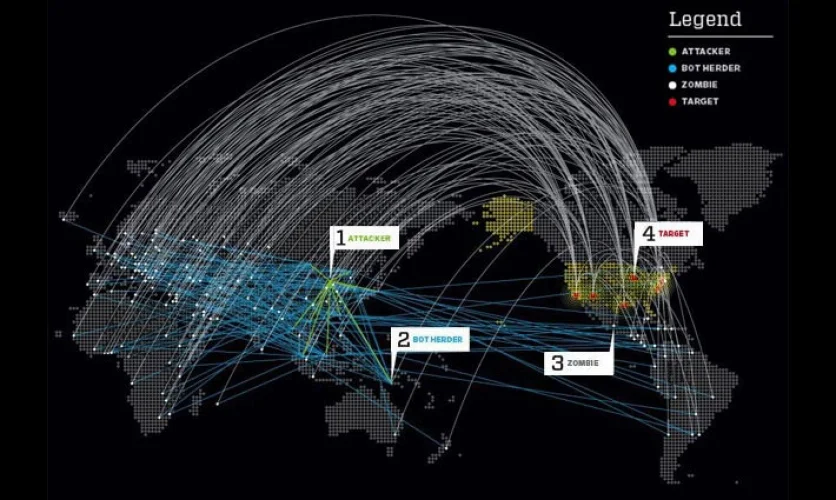
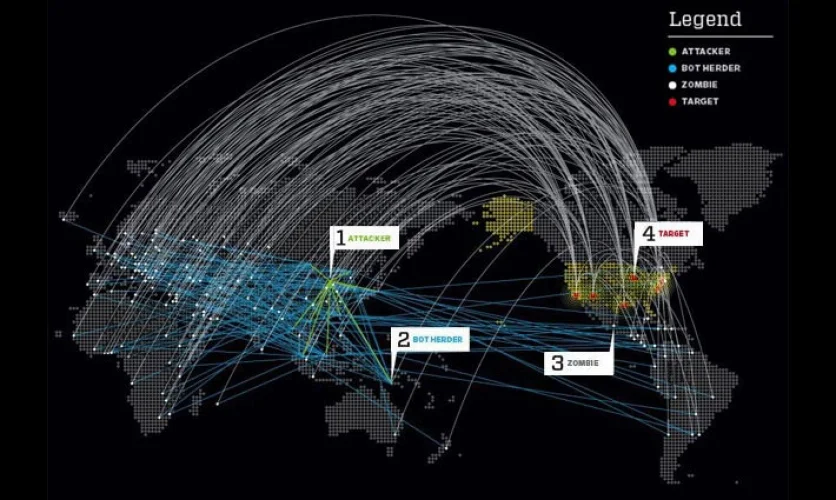
How to Protect Your Business from DDoS Attacks
DDoS protection basically refers to a succession of actions that endeavor to protect the network against potential DDoS attacks. Many people ask why it is important to have the network protected against DDoS attacks. This is a common question because most people are not aware of the risks and possible damages associated with DDoS attacks. DDoS protection plans can only be appreciated by people who are conscious of the destruction caused by such attacks.
How Are You Shielding Your Business Against the Threats Related to Web Applications?
Web applications have been in trend for a while now and they keep on advancing. They have perhaps penetrated all the crucial segments of our daily lives that include our corporate and business world as well. Business applications related to accounting, customer relationship Management, collaboration, Enterprise Resource Management, online banking, content management, E-commerce are now all made available on the Internet. Web Applications have played a vital role in increasing speed and accessibility to all kinds of business information for an enterprise’s clients, partners and employees. They have also assisted in allowing savings. Today, not only have most things shifted to the web but almost all of them host a business’ most sensitive and valuable data.